RP2350 Microcontroller Security Hacked
on
The Challenge
Announced at DEF CON 32 in August 2024, the RP2350 Hacking Challenge was a collaboration between Raspberry Pi and security specialists at Hextree.io. Participants were tasked with extracting a secret programmed into the OTP memory of the RP2350, a microcontroller boasting security features like Secure Boot, ARM TrustZone, glitch detectors, and a custom Redundancy Coprocessor (RCP). The challenge’s purpose was to stress-test the chip’s protections under real-world conditions.
Enter Aedan Cullen

Engineer Aedan Cullen demonstrated an attack at the 38th Chaos Communication Congress (38C3), bypassing key security features to access protected data stored in the chip’s one-time programmable (OTP) memory. Raspberry Pi has not yet confirmed if Cullen’s exploit constitutes the winning entry in its $20,000 Capture the Flag challenge, with the official announcement scheduled for 14 January.
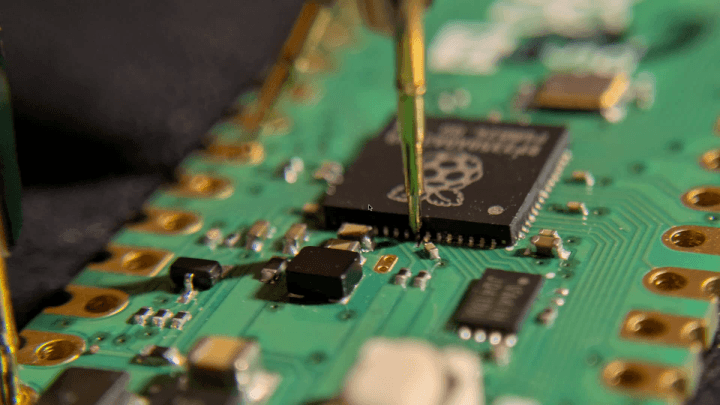
Cullen’s approach leveraged a voltage injection glitch on Pin 53 (USB-OTP_VDD), a critical connection to the chip’s OTP functionality. By inducing a brief 50 μs voltage drop during specific reads of the OTP memory (CRIT0 and CRIT1), Cullen was able to reactivate “permanently disabled” RISC-V cores and gain access to the debug port. This allowed him to extract the secret from the otherwise locked OTP memory. It’s an ingenious attack that shows how even seemingly minor design decisions — like the handling of specific voltage rails — can create exploitable weaknesses.
Technical Highlights
- Timing: Cullen synchronized the glitch with a critical 600 μs startup sequence using Python scripts to sweep the voltage drop’s timing.
- Tooling: A modified RP2350 board allowed Cullen to isolate and manipulate Pin 53.
- Debug Access: The glitch bypassed the chip’s security mechanisms, enabling access to debug features normally locked down by Secure Boot.
Cullen’s method is both crazy sophisticated and remarkably practical. Thorough documentation analysis, combined with hardware experimentation, helped him exploit vulnerabilities that might seem far-fetched on paper. His use of scripting to pinpoint the exact glitch timing demonstrates how technical precision can turn theoretical weaknesses into tangible exploits.
Broader Implications
The RP2350’s security architecture — a major improvement over the previous RP2040 model — was intended to meet the demands of industrial and commercial users requiring strong protection. However, Cullen’s hack demonstrates that even robust security features can have overlooked flaws. This raises valid concerns about whether the RP2350’s protections are sufficient for high-security applications or whether additional layers of defense are needed to safeguard sensitive systems.
Awaiting Confirmation
While Cullen has shared his findings publicly, including annotated diagrams and source code on GitHub, Raspberry Pi has yet to confirm whether his method is the winning entry. The official announcement is expected on 14 January 2025. If validated, Cullen’s exploit may prompt Raspberry Pi to revisit the RP2350’s security design or issue firmware updates to mitigate the vulnerability. We’ll see!








Discussion (0 comments)