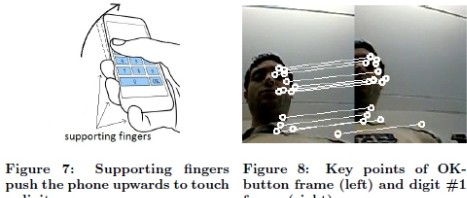
| Here we build a low-cost contactless door-entry system and use some clever software to evaluate the resonant behavior of a standard security...
More about Security (144)
| In the same week British Prime Minister Cameron proposed a ban on encryption “to keep our people safe”, Der Spiegel revealed that the NSA us...
| As the energy landscape goes through significant changes both in the European Union and outside its borders, the EU finds itself in the midd...
| Ubiquitous sensors, tell-tale WiFi signals, smart meter information, always-on wearable technologies and the roll-out of networked Internet...
| In a report by theUniversityofCaliforniain 2011 researchers developed the TouchLogger malware App to show that information from a phone’s ac...
| After 1.5 years of work hackers Bunnie Huang and Sean 'xobs' Cross have working prototypes of an open source laptop. Specs and source files...
| Armed with a Raspberry Pi and a wireless adapter extension two hackers show how surprisingly easy it is for an attacker to take control of a...
| CyanogenMod, a community built distribution of Android, has teamed up with Open WhisperSystems to provide user friendly cross-platform encry...
| Lavabit and Silent Circle, two secure email providers, launched the Dark Mail Alliance with the aim to provide private and secure email. Cen...
| By blowing off the Nabucco gas pipeline project as Europe’s fourth energy road, the BP-led Shah Deniz consortium sank a flagship of the EU’s...