| A thermal runaway is an increasing threat to electronic devices where more and more power is packed in ever smaller spaces; it is a threat t...
More about Security (144)
| Microchip announces the ATECC608A CryptoAuthentication™ device, a secure element that allows developers to add hardware-based security to th...
| Engineers from the Rutgers University in New Jersey have developed an identification system that detects the vibrations in a finger in order...
| For little cost it is possible to add the GT-521F52 fingerprint scanner to a microcontroller, an Arduino, a Raspberry Pi, a computer, or to...
| Hajime is the name of a malware — a worm — that is currently infecting thousands of devices connected to the public Internet. The worm mainl...
| In close cooperation with PRQA, Elektor is offering a free download of three high-quality papers on how to create secure embedded software....
| Improve software security; reduce development time
| With an expected 500 billion connected devices in 2022, we can't secure the Internet of Things on the device level, said Professor Frank Fit...
| Are your communications secure? There are many overhyped "cryptophones" and crypto software programs available today, but can you really tru...
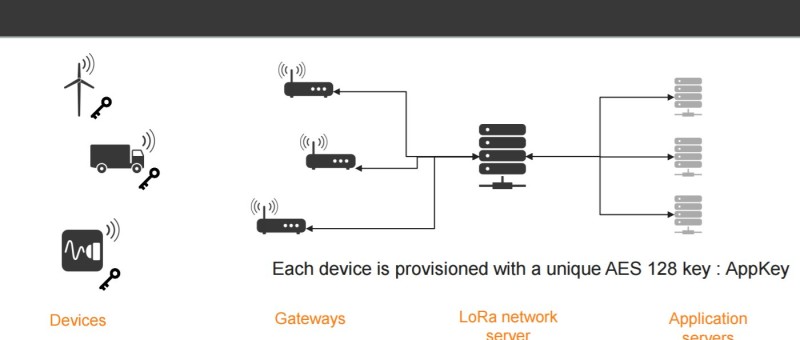
| Certain documents from the LoRa Consortium show that LoRaWAN uses the AES 128 algorithm to encrypt messages. However, according to French IT...